Counter Corporate or Economic Espionage
Corporate or economic espionage is the unlawful theft/acquisition of intellectual property, such as key trade secret and patent information as well as industrial manufacturing techniques and processes, ideas and formulas. It could also include sequestration of proprietary or operational information, such as that on customer...
Structural Resilience Study (SRS) & Blast Effect Analysis (BEA)
Structural Resilience Study (SRS) is a specialised engineering study to determine the weapon and blast effects of an attack, structural responses and structural vulnerability of any given structure element of a building under a planning parameters of blast, shock and impact loads generated from a...
Project Management (PM)
AIP’s project managers are experienced in managing security implementation projects across various industries, from small scale projects to large scale projects with high contract value. A project management scope of work for a security project during the implementation stage comprises of project initiation, project planning, project...
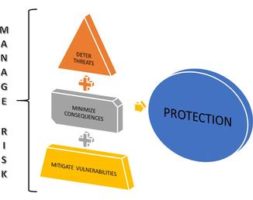
Threat, Vulnerability and Risk Assessment (TVRA)
AIP Risk Consulting uses a risk-based approach; Threat, Vulnerability and Risk Assessment (TVRA) to protect critical infrastructure and critical assets, tailored towards and applied on an asset, system, network, or functional basis, depending on the fundamental services it is intended to support and the nature of the related...
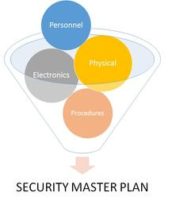
Security Planning
Organisations today constantly fail to recognise the need to identify and assess their risk exposure, before implementing security measures and/or technology. It is simple to install a set of security system and considered that the threats are mitigated. Little thoughts and efforts have been put in...
Security System Design
AIP RIsk Consulting specialises in devising customised security solutions to solve customer’s problems, increase security productivity, reduce security expenditure and enhanced overall security provisions in customer’s facility. AIP Risk Consulting approaches customer’s problem head on with an initial analysis and review of the weaknesses in the system and operational...
Security Audits
A physical security survey is a practical process utilized to evaluate specific areas, applications, or processes of a facility site to document potential threats and security vulnerabilities and/or validate the security plan in place. The survey can be performed from a threat-based perspective, physical security,...
Tender Documentation & Evaluation
In the tender documentation preparation stage, all necessary documents in accordance to the accepted security recommendations will be prepared as part of the main tender documents for the purpose of inviting tenders for the supply, installation and implementation of the security measures. This process will...