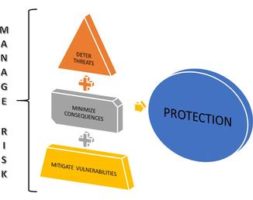
Managing Security Risk
With increasingly challenging transnational business operations, securing your businesses from operational and technology risks is one of the top priority for any organisation’s leaders to minimize disruption to businesses incurring consequences such as losses of life, intellectual property, physical assets and reputation. Leaders need to be updated on the presence of any business risk by identifying threats (or risk causes), evaluating the effectiveness of existing control mechanism, analyzing the damages/ impact, using semi-quantitative risk assessment approach. The risk derivation shall be used as a basis in the selection of appropriate and sound mitigation measures.
Threats ranging from global terrorism to workplace violence have forced companies and institutions to take a closer look at their security plans. In some sectors or industries, a business or organisation may be hinged to the factor of having excellent security measures to build its reputation and attract customers. In the event of a terrorist attack or criminal breach, if the business or organisation is not capable of fulfilling its legal obligations and/or business continuity plans, the business or organisation will lose its good name. The resulting loss of reputation may adversely affect your business.
Our Core Services
QUALIFIED PROFESSIONALS
OUR CONSULTANTS HAVE THE CREDENTIALS, SKILLS AND EXPERIENCES.
Our professional team of consultants includes Certified Protection Professional (CPP), Certified Business Continuity Professionals and qualified engineers.
We have specialised expertise in solving security challenges and devising security solutions tailored to meet customers’ needs.

Our Clients and Partners